
Meet Your Security Engineer
Hello! I’m Abubakar, a dedicated Security Engineer with 8+ years of experience in protecting digital infrastructure and defending against cyber threats. My mission is to help organizations build robust security postures through proactive assessments, rapid incident response, and strategic defense solutions tailored to your unique risks.
Why Clients Trust Me
Clear Communication, No Technical Jargon
Security doesn't have to be confusing. I explain risks and solutions in plain language that makes sense to both technical teams and business leaders.
Tailored Solutions for Your Business
No cookie-cutter approaches. I take time to understand your specific needs, risks, and goals, then build security strategies that fit your organization.
Compliance & Standards
Security isn't just about code; it's about rules. I ensure your infrastructure meets industry standards (like GDPR, ISO, or NIST) to keep you legally safe and compliant.
Rapid Incident Response
Time is critical during a breach. I provide rapid response strategies to contain threats immediately, minimizing downtime and protecting your sensitive data.
Cost-Effective Security
Security shouldn't bankrupt your business. I prioritize high-impact, cost-effective solutions that maximize your protection without unnecessary spending on bloatware.
Offensive Security Mindset
To beat a hacker, you must think like one. I use offensive security techniques to identify and patch vulnerabilities before malicious actors can exploit them.
Let's Secure Your Peace of Mind
Regulatory Compliance
2025

Incident Response Planning
2025

Employee Security Training
2025

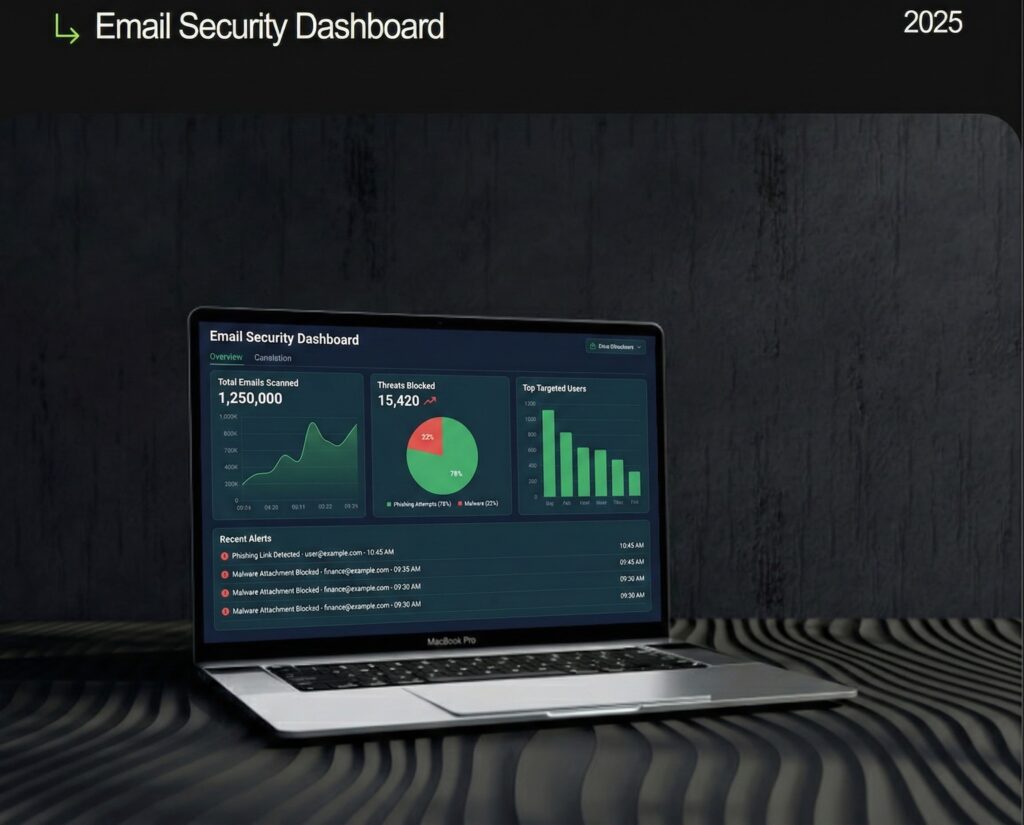
Email Security
2025
Vulnerability Consulting
2025

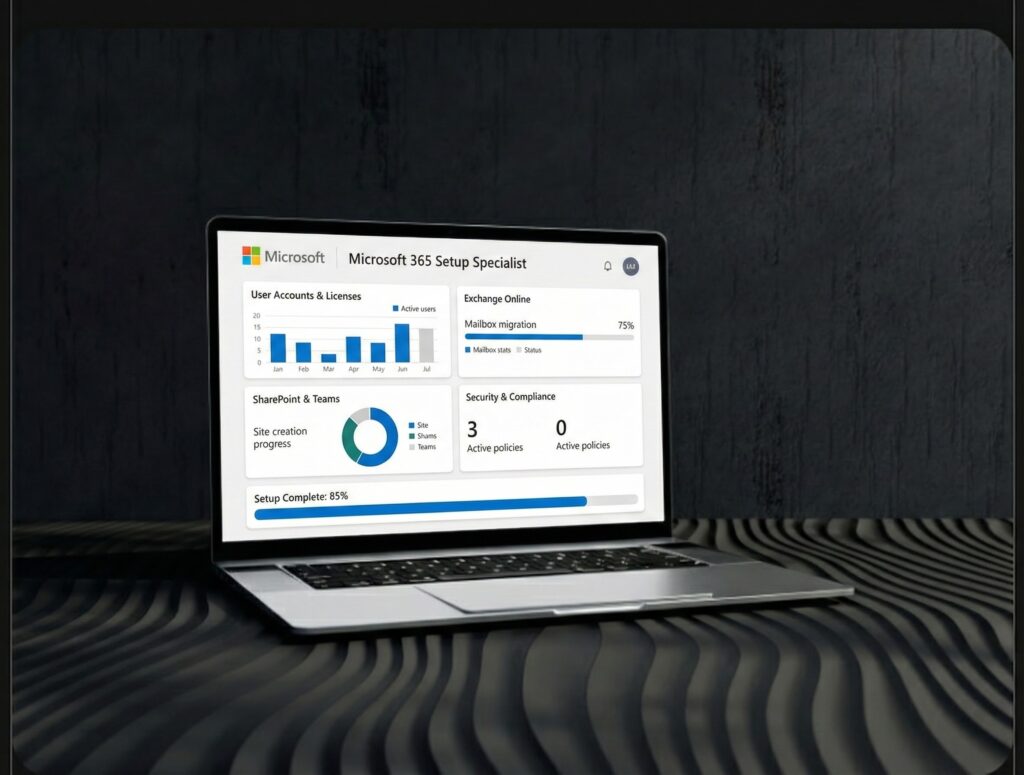
Microsoft 365 Setup Specialist
2025
My Security Process

1. Discovery & Assessment
I start by understanding your business, current security posture, and specific risks. Through detailed consultations and initial scans, I identify vulnerabilities and prioritize what needs immediate attention.
2. Strategy & Planning
I develop a comprehensive security roadmap tailored to your needs. This phase focuses on designing defense layers, selecting the right tools, and creating actionable plans that align with your business goals.
3. Implementation & Hardening
I execute the security strategy—deploying protections, configuring systems, patching vulnerabilities, and integrating security into your workflows. Every solution is tested to ensure it works seamlessly without disrupting operations.
4. Monitor & Evolve
I continuously monitor your environment for threats and provide ongoing support. Post-implementation, I deliver regular reports, conduct periodic assessments, and adapt defenses as new threats emerge to keep you protected long-term.
08+
Years of Experience
Proven track record in cybersecurity and threat management.
15+
Clients Protected
usinesses secured with proactive defense strategies.
98%
Client Satisfaction
Delivering security solutions that exceed expectations.
